Understanding Amazon GuardDuty

For past few months, I have been exploring some niche fields of cybersecurity such as malware analysis & threat intelligence. I have been reading a lot of articles and learning about new tools related to them. In this blog, I will be briefly talking about one of the widely used threat detection service by AWS, Amazon GuardDuty. This blog (it’s more of a entry in my personal journal) will not be that technical, just a brief overview of the service. Following topics are covered in this blog:
Table of Contents
- Introduction
- What exactly is threat detection?
- What is Amazon GuardDuty?
- How does Amazon GuardDuty work?
- Detecting & Classifying Findings
- Integrating Amazon GuardDuty with Other AWS Services
- Threat Response Scenario
- Conclusion
Introduction
Just now I mentioned CTI in the introduction. So, what does CTI stands for? CTI stands for Cyber Threat Intelligence. It is the process of collecting and analyzing information about adversaries and their motives, intent, and capabilities to inform decisions, mitigate risk, and take action. CTI is a very broad field and it is not possible to cover everything in this blog. I will be writing a separate blog on CTI in future. For now, let’s focus on threat detection and Amazon GuardDuty.
What exactly is threat detection?
Before we start talking about threat detection, let’s first understand what is a threat. A threat is a potential danger that can exploit a vulnerability to breach security and cause possible harm. Threats can be classified into two categories: external and internal. External threats are the ones that originate outside the organization. For example, a h4ck3r trying to gain access to your network. Internal threats are the ones that originate inside the organization. For example, an employee trying to steal sensitive data.
Now, let’s talk about threat detection. Threat detection is the process of identifying threats that are trying to exploit vulnerabilities in your network. It involves monitoring your network and systems for indicators of compromise (IOCs) that could signal a potential threat. Common IOCs include suspicious IP addresses, domain names, file hashes, and network traffic patterns. The types of threats that can be detected vary widely, from malware infections and phishing attacks to insider threats and advanced persistent threats (APTs). Effective threat detection requires a combination of human expertise and advanced technologies, such as machine learning and behavioral analysis.

Ultimately, threat detection is an ongoing process that requires constant vigilance and a commitment to staying up-to-date with the latest threats and attack techniques. By implementing a comprehensive threat detection strategy that includes both human expertise and advanced technologies, organizations can reduce their risk of a successful cyber attack and protect their valuable assets and data.
What is Amazon GuardDuty?
According to official documentation of Amazon GuardDuty provided by AWS:
“Amazon GuardDuty” is a threat detection service that continuously monitors for malicious activity and unauthorized behavior to protect your Amazon Web Services accounts, workloads, and data stored in Amazon S3.

Amazon GuardDuty is a cloud-based security service that provides automated threat detection and response capabilities for AWS environments. It enables CTI analysts to identify and prioritize potential threats quickly by analyzing data from various sources, such as AWS CloudTrail and VPC Flow Logs, using ML algorithms and threat intelligence feeds. This allows analysts to focus their efforts on investigating and mitigating real threats, rather than spending time on false positives or manually combing through data.
How does Amazon GuardDuty work?
Amazon GuardDuty uses a combination of machine learning algorithms, anomaly detection, and threat intelligence feeds to analyze data from multiple sources, including AWS CloudTrail, VPC Flow Logs, and DNS logs. It looks for patterns and anomalies in the data to detect potential threats, such as network scans, port probing, and data exfiltration attempts. It also uses threat intelligence feeds from AWS and third-party sources to identify known indicators of compromise, such as IP addresses and domains associated with malicious activity. It continuously updates its threat intelligence feeds to stay ahead of emerging threats.
When GuardDuty identifies a potential threat, it generates a security finding and sends it to the AWS Security Hub or to an SNS topic for further processing. The security finding contains information about the threat, including the type of activity, the affected resource, and the severity of the threat. You can then take action to investigate and remediate the threat.

How to setup Amazon GuardDuty?
Setting up Amazon GuardDuty is very easy. You can enable it with just a few clicks in the AWS Management Console. But it all depends on your use case. If you want to enable it for your entire AWS account, then you can enable it with just a few clicks. But if you want to enable it for a specific region or a specific VPC, then you will have to do some additional configuration. More details about this can be found in the official documentation of Amazon GuardDuty.
Detecting & Classifying Findings
It is important to understand that GuardDuty is not a replacement for your existing security tools. It is a complementary service that can be used to detect threats that are not detected by your existing security tools. For example, if you are using a firewall to detect network scans, then GuardDuty can be used to detect port probing attempts that are not detected by your firewall. Similarly, if you are using an IDS to detect malware infections, then GuardDuty can be used to detect phishing attacks that are not detected by your IDS.
GuardDuty provides a number of built-in threat detection capabilities, including the following:
- Network Scanning
- Port Probing
- Malware Infections
- Phishing Attacks
- Data Exfiltration
- Denial of Service Attacks
- Credential Stuffing
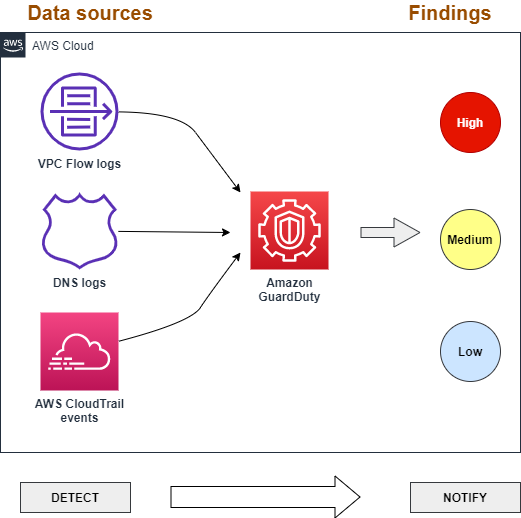
Irrespective of the type of threat, GuardDuty classifies each threat into one of the following categories:
-
Low Severity: These findings indicate a potential security issue that requires further investigation, but are not immediately critical or urgent. Examples of low severity findings include unusual network traffic or access attempts from suspicious IP addresses.
-
Medium Severity: These findings indicate a more serious security issue that requires prompt action. Examples of medium severity findings include attempted privilege escalation or suspicious activity that could indicate an insider threat
-
High Severity: These findings indicate a critical security issue that requires immediate action to prevent significant damage to your AWS environment or data. Examples of high severity findings include malware or ransomware infections, compromised instances, or unauthorized access to sensitive data.
- Informational
- Undefined
Integrating Amazon GuardDuty with Other AWS Services
Integrating Amazon GuardDuty with other AWS services, such as AWS Security Hub, can help you streamline your security operations and gain deeper insights into your security posture. You can also integrate GuardDuty with third-party security tools, such as Splunk, to gain additional visibility into your security posture.

By integrating GuardDuty with AWS Security Hub, you can get a unified view of your security posture across all your AWS accounts and regions. You can also use Security Hub to prioritize and manage security findings generated by GuardDuty. You can also use Security Hub to automate the response to security findings by integrating it with other AWS services, such as AWS Config, AWS CloudWatch Events, and AWS Lambda.
Note: You can integrate it with Jira, ServiceNow, and Slack to get notifications about security findings. This can be very useful for ticketing and incident management.
Threat Response Scenario:
I have tried to introduce GuardDuty in the previous section. Now, let’s see how it works in a real-world scenario from a perspective of a novice CTI analyst. Let’s say you have an AWS environment with a web server running in an EC2 instance that’s connected to an Elastic Load Balancer (ELB) and has a MySQL database instance running in RDS. You have also enabled GuardDuty in your account to detect any malicious activities in your environment.
Now, imagine that GuardDuty has detected a potential threat where an attacker is attempting to brute force the credentials to gain unauthorized access to the MySQL database instance. GuardDuty will generate a security finding and send it to the AWS Security Hub. The security finding contains information about the threat, including the type of activity, the affected resource, and the severity of the threat. You can then take action to investigate and remediate the threat.
I know that was a very abstract example. But I hope it gives you an idea of how GuardDuty works in a real-world scenario. There are many other scenarios where it can be used to detect and respond to threats in your AWS environment. Using GuardDuty, you can explore these scenarios and learn more about how it works.
Conclusion
As a complete beginner, I have tried to introduce Amazon GuardDuty in this article. No tool is perfect. GuardDuty is no exception. It has its own limitations. There are many other tools that can be used to detect and respond to threats in your AWS environment. But GuardDuty is a good place to start.
I hope you have found it useful. In future articles, I will explore more advanced topics related to Cybersecurity, such as reverse engineering, binary exploitation, malware analysis, advanced OSINT, threat hunting and threat intelligence. Stay tuned!
